
How to Hack Wi-Fi: Cracking WPA2 Passwords Using the New PMKID Hashcat Attack « Null Byte :: WonderHowTo

2500 - WPA-EAPOL-PBKDF2 (Iterations: 4095) Kernel Build Failure MacOS 10.14.5 · Issue #2076 · hashcat/hashcat · GitHub
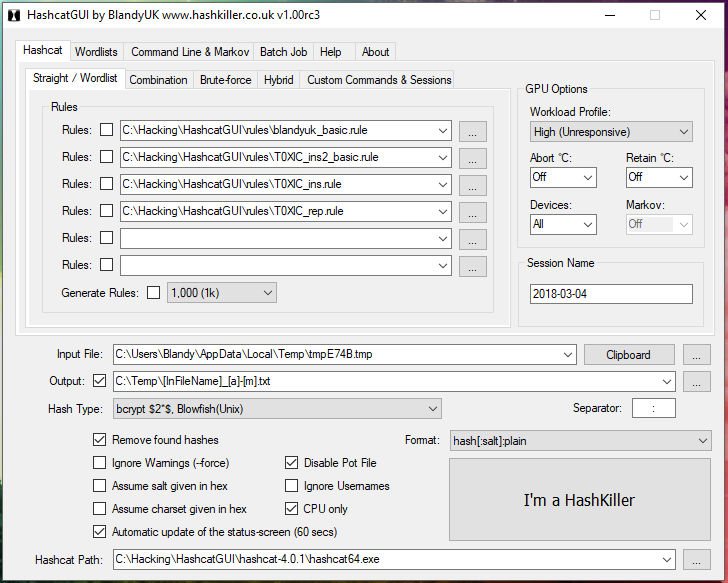
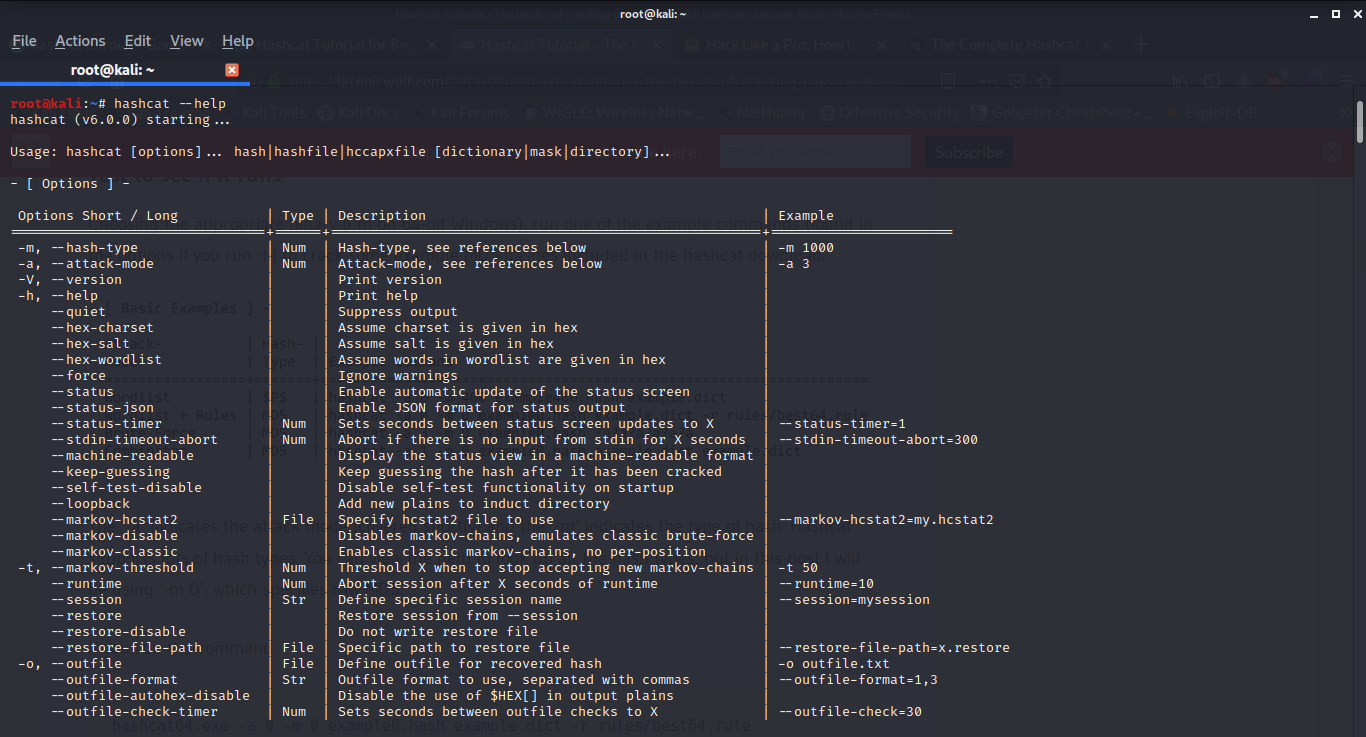
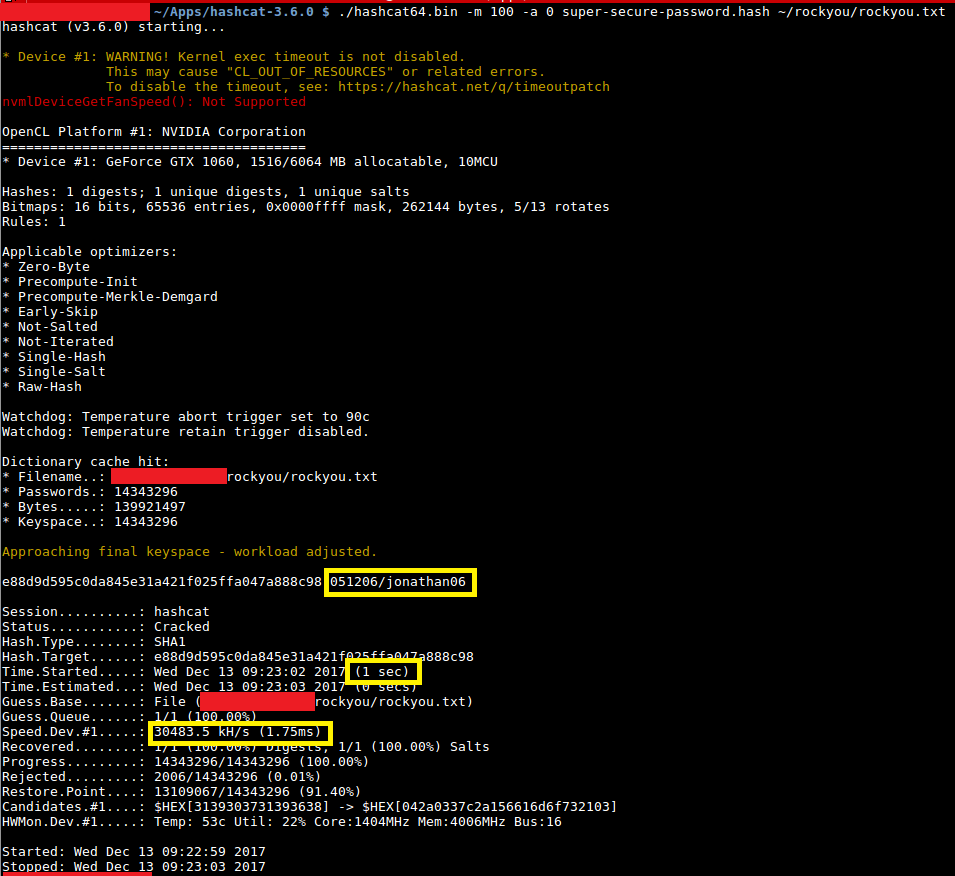
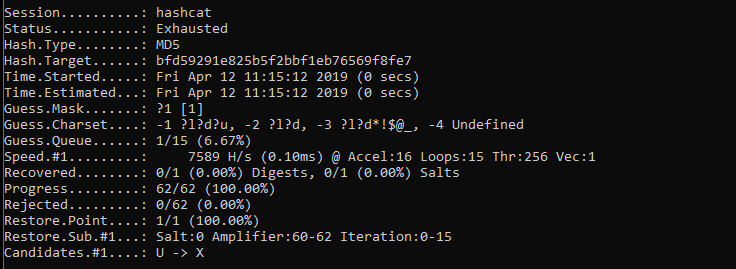
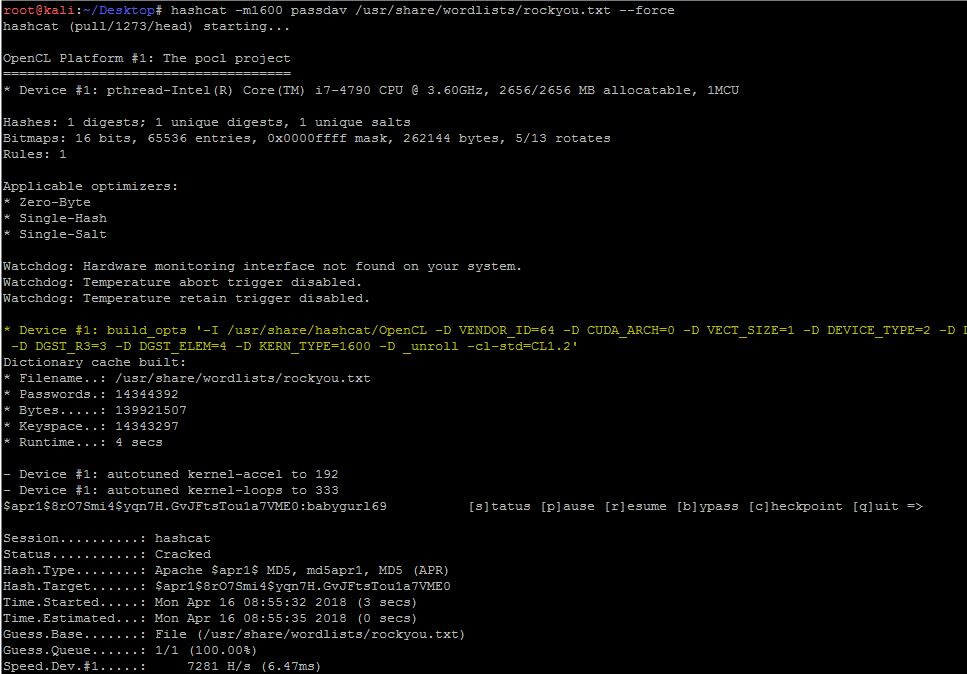
Hashcat manual: how to use the program for cracking passwords - Ethical hacking and penetration testing
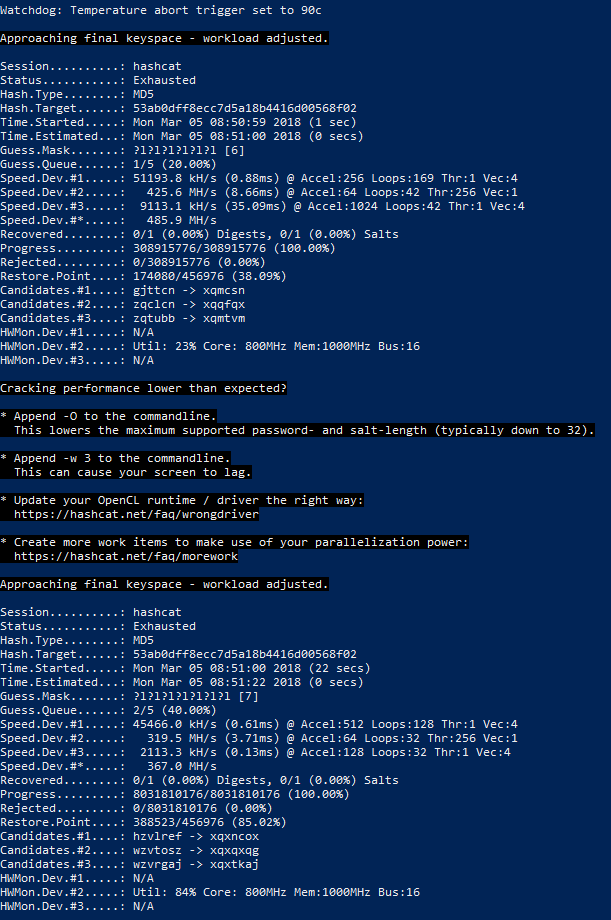
Hashcat manual: how to use the program for cracking passwords - Ethical hacking and penetration testing

Hashcat manual: how to use the program for cracking passwords - Ethical hacking and penetration testing
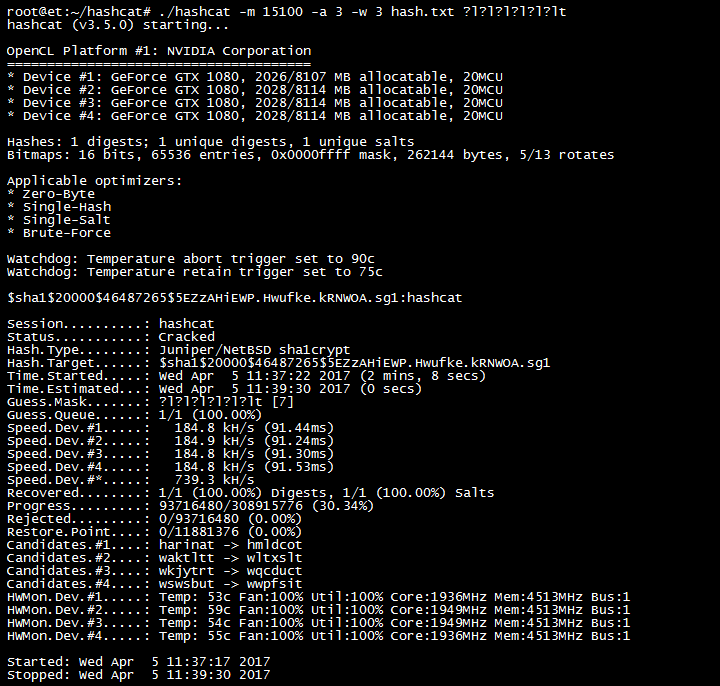
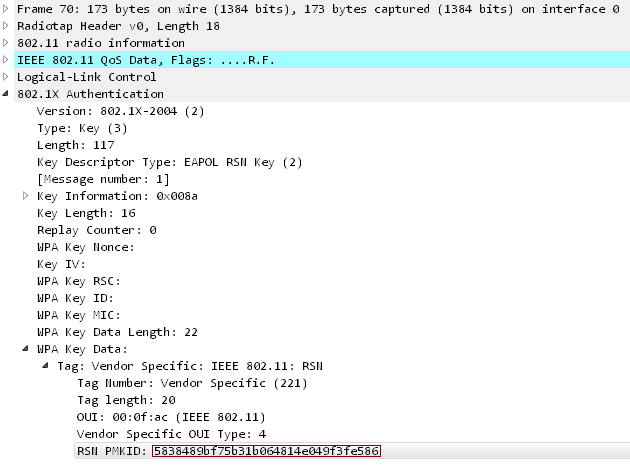
![hack wpa/wpa2 via PMKID new tech [snmafia:trailer]] - YouTube hack wpa/wpa2 via PMKID new tech [snmafia:trailer]] - YouTube](https://i.ytimg.com/vi/8kRuE4un_kQ/hqdefault.jpg)

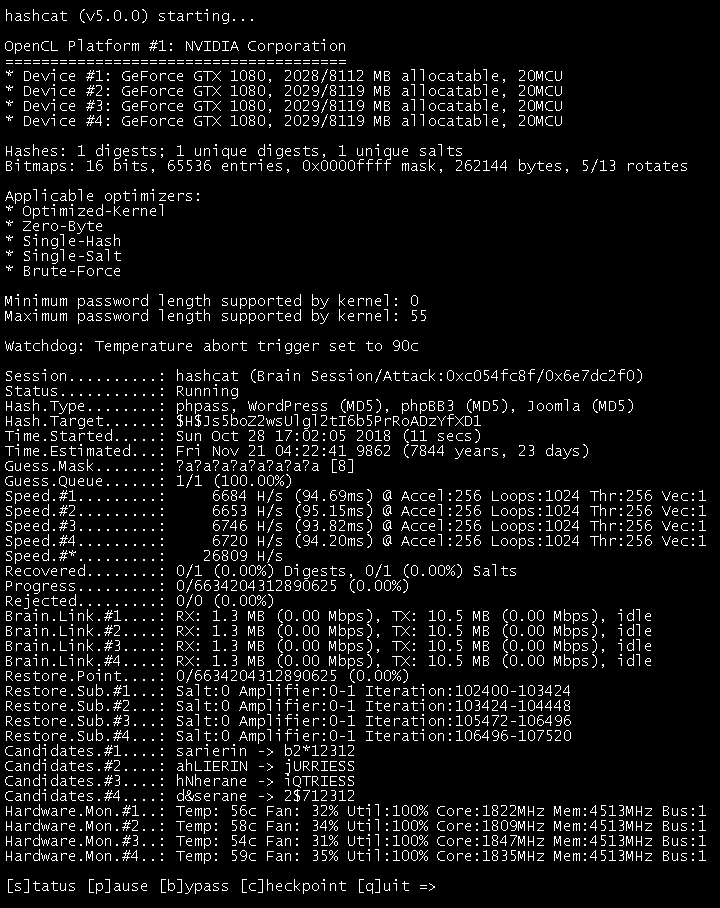
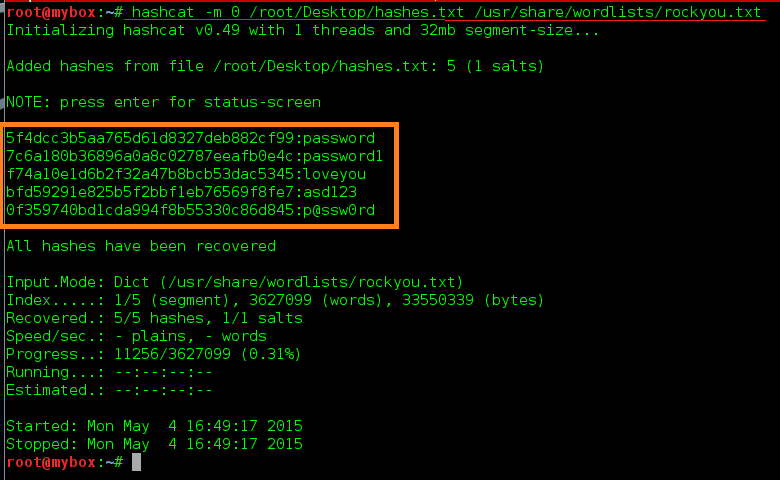

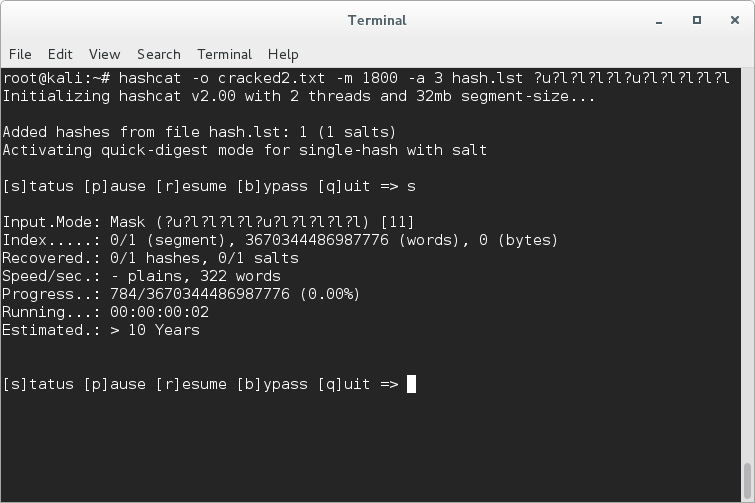
![hashcat [hashcat wiki] hashcat [hashcat wiki]](https://hashcat.net/wiki/lib/exe/fetch.php?tok=505d08&media=https%3A%2F%2Fhashcat.net%2Fhashcat%2Fhashcat.png)


